IT Support Blog
Peter Heinicke
Recent Posts
A complimentary assessment of your cloud computing capabilities
Posted by Peter Heinicke on 8/14/24 11:00 PM
Source: MastersInIT.org
If you’re in the market for a career change or still in school and thinking about your future, consider the growing economy around Big Data and Data Science. It’s not just for computer programmers, mathematicians and statisticians — though that’s a strong factor — but also for business strategists, graphic designers and many more. In fact, Big Data will affect many aspects of our lives and Data Science will require new ways of thinking about all the information that we collect.
Tags: Redundancy, data extraction
All companies need to be prepared for emergencies; however, there are an astounding percentage that are not. If some sort of catastrophic event were to happen, would your company be ready? Do you have a disaster recovery plan in place that will get you through? Keep in mind that the term 'Disaster' applies to many different types of events, not only encompassing events brought by mother nature, but also accidental, or deliberate human influence such as fire, flood, a loss of communication or even a virus. In order to ensure total preparedness, there are two important key plans you should consider. The first is a Business Continuity Plan (BCP), and the second a Disaster Recovery Plan (DRP). While the two have many things in common, the main differentiator is that a DRP focuses on recovery whereas a BCP allows for continued business until recovery is accomplished.
There are several steps to take in order to build your BCP and DRP plans and we've included some tips below on how to get started. Your peace of mind and the future of your company is of the utmost importance and we hope you find this information helpful.
Tags: IT services, DR, Disaster Recovery, Redundancy, Backup
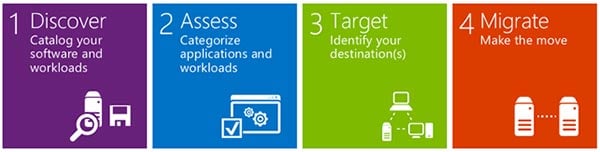
View: Move and Modernize Your Workloads with Azure
Read MoreData Governance for GDPR Compliance: Principles, Processes, and Practices
Posted by Peter Heinicke on 12/18/18 11:02 AM
Tags: gdpr
It's easy to look like a pro. Create professional-looking invoices from anywhere--thanks to more than 100 templates provided in Office 365.
Read MoreAutomated tools like anti-virus software, firewalls, and other computerized security technology can only go so far to eliminate the threat posed by a small army of professional hackers. Like most crimes, the human element is critical for the cyber crime to be successful. To combat this, I sorted out 7 urgent reasons why you need to create your "human firewall" as soon as you possibly can. Employees are your last line of defense and need to become an additional security layer when attacks make it through all your technical filters.
Your users need to be trained to become a human firewall against cyber attack
- Phishing leads the IRS dirty dozen of scams
- Phishing is the use of phony email to obtain information or compromise systems. The Internal Revenue Service rounded up some of the usual suspects in its annual look at the Dirty Dozen scams you need to watch out for this year. It should come as no surprise that the IRS saw a big spike in phishing and malware incidents during the 2016 tax season because the agency has been very public about its battle with this scourge.
Read More
Tags: Anti Virus, ransomware, phishing, vishing, spam
Tags: Microsoft, Office 365, software as a service, subscription licensing
Windows, rocks
I am truly impressed:
The past few releases of Windows have been a game of give and take. You gave the OS more resources and money, and got more features and security. Meanwhile, older hardware sets had to go in the recycle bin before they were actually worn out. Useful, but no longer in production software sets had to be replaced because they no longer worked on the new releases of Windows. Windows 10 is better than XP, Vista, 7, 8, and 8.1 for a lot of reasons, and mainly because it performs much better than expected in the compatibilty and performance area, and because it is available to be activated for free to users with the home and pro editions of Windows 7, and 8.x. (Enterprise users still have to pay). What's more, the download and upgrade process is pretty painless, and I am 4 for 4 upgrading hardware which is from 5 to 7 years old to a working version of Windows 10. Recalling Hubert Humphrey, "I am pleased as punch". There are more reasons than this brief paen to upgrade and I will list them below.
Read More
Tags: upgrades, user interface, windows 10, OS Design, Windows 10 review
Tags: Backup, Software Obsolescence | accounting systems | ERP S
On Saturday, April 26, 2014, Microsoft Corp. reported to the United States Computer Emergency Readiness Team (a division of the Department of Homeland Security) that Microsoft Internet Explorer versions 6-11 had come under attack! Malicious hackers were exploiting a use-after-free vulnerability that could allow unauthorized remote code execution. This could lead to the complete compromise of an affected computer system.
Tags: Blogging, Blog, IT Support, Anti Virus, Microsoft, Internet Explorer
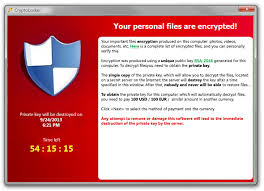
Tags: Disaster Recovery, Backup, Backup to the cloud, Symantec, CryptoLocker, Managed Services
Tags: Backup, Backup to the cloud, Anti Virus, Symantec, Malware, Security Software, CryptoLocker, ransomware
Tags: IT services, Shareware, Blogging, Blog, Article Publishing, IT Support, Tablet Computer, Customer Engagement, Web Content, targetted Marketing
The clock is ticking: Is your Windows XP migration plan ready ...
Posted by Peter Heinicke on 9/27/13 1:15 PM
We all know that technology marches every onwards, and these challenges present us with an opportunity for growth, but two migrations at the same time? How are we to make sense of that? Although the Windows XP migration has been on the cards since its release, with the termination of support being a planned strategy, it can represent a major challenge for many businesses. Migration can take 18 to 32 months to get right, and - depending on the size of your business - is not always something that your IT department can handle alone. For large businesses, it's simply too great a task.
Centrica, the British multinational utilities company, plans to migrate 26,500 staff from Windows XP to Windows 7 by the end of the year. It's a $65 million move, and Centrica have had to bring in Fujitsu to manage it. And it's not just Windows XP that will become obsolete, but also Office 2003 and XP SP3. Migration on such a scale brings to the fore various questions about how we manage our desktop IT. It could be just the right kind of move that forces many businesses, large and small, to reassess their IT strategy.
No matter the size of your business, running an unsupported operating system is simply not viable. From April 8, 2014, all free and paid support for Microsoft Windows XP, XP SP3 and Office 2003 will cease. Security updates and non-security hot-fixes will no longer be available, and your IT infrastructure will be wide open to, and likely plagued by, errors, bugs and attacks. You're looking at potentially wide-spread control failure, suspended certificates and licenses and an inability to protect your customer's and client's personal information. These short-comings will be both an internal nightmare and public knowledge. It forces us to confront our IT strategies head-on, and leaves us asking ourselves how to address all of these challenges at once.
While it may be possible to install Windows 7 or Windows 8 into your XP OS, you'd be playing a dangerous game of dicing with unavoidable obsolescence. The benefits of migrating to a Windows 7 system are obvious, given the short-comings and impending redundancy of Windows XP. Migrating to Windows 7 will afford your staff a more flexible, dependable and efficient system. It will improve operational efficiency, and put you back in the drivers seat until Windows 7 itself becomes unsupported in 2020. Windows 8 is also an option, but Windows 8 has alarming and widely recognized deficiencies. Support for Windows 8 will continue until 2023, but since we are already considering a whole-scale migration we may as well consider the best possible migration.
PC manufacturers are cottoning on to this industry-wide upheaval and are pushing Windows 8 into businesses by offering it at a far cheaper price than Windows 7. You can pick up a Windows 8 PC with 6 GB of memory and a 1 TB hard drive for as little as $330 to $400. The cost of new hardware has actually fallen significantly in the last two quarters as manufacturers attempt to promote new hardware as as an enterprise worthy solution to the migration. It's possible they have a point, as the 'hardware is the new software' debate continues amid the increasing popularity of hybrid devices, and as features like touchscreens and SSD drives become more common.
Some businesses have decided to roll out new internet-centric operating systems to departments like sales and marketing, where staff aren't dependent on things like MS Office. Many people are seeing the Windows XP migration as an opportunity to upgrade their hardware, or trial newer operating systems like the linux derived Chrome OS which runs on the internet-centric Chromebook and Chromebox. These are low-cost, low-maintenance solutions that have the advantage of security being managed from the internet gateway, for example, making the IT environment easier to manage and raising the possibility of cloud-based solutions being the way forward. More and more of our clients have been switching to cloud servers rather than replace their 2003 servers. Unlike the Microsoft servers, cloud servers have no planned expiration date and could conceivable keep running forever, so long as there is a way to power them.
Tags: St. Charles PC Repair, Windows XP, Windows 7, Windows 8, PC Migration, IT Support, Software Obsolescence | accounting systems | ERP S
How does one become CIPA compliant? If you just block a list of websites, it won't work because the bad guys are always jumping from url to url and it would be an impossible chore for one person to scan the net for all sites of a banned category. So, you go out and buy a filtering and/or blocking device that plugs into the system between where your internet service enters the building and the first router in line after that. These usually (but not always) come with a subscription to monitor the incoming material and check it against a constantly updated list of banned websites. WebSense will sell you a server, for several thousand dollars or more, complete with custom CIPA compliant programming for your particular school or library, which includes the subscription. Sounds ok, right? Surprise, you are still not CIPA compliant! Yes, you have stopped all of the incoming questionable material and have severely restricted the kids’ access to Facebook and other social media while at school. At the same time you have restricted You Tube, but can still use it for selected very good and educational videos on You Tube. But YOU ARE STILL NOT CIPA COMPLIANT!
Tags: Blogging, Blog, Web Content, Symantec, Security Software, Website Traffic
IT Wars: Episode 1 - Removing unwanted Anti-Virus software
Posted by Peter Heinicke on 8/6/13 11:52 AM
Tags: Disaster Recovery, Network Consulting, Fox Valley PC Support, Anti Virus, Virus Removal, computer repair
Q & A - Can you turn an SBS 2003 server into a workstation?
Posted by Peter Heinicke on 2/8/13 9:47 AM
Question:
I have an SBS 2003 server with 16 gb of ram, which I would like to demote to a workstation type function on a network with Windows 2008 Server. How could one do that. I'd rather not wipe and reinstall windows 7 64 bits.
Server is about 3 years old.
Answer:
An SBS server can't be a member server. It must hold the FSMO roles and if it doesn't it will reboot on a regular basis. You will also have licensing issues in that if you only run Windows and do not make it a DC or full blown SBS server, the license will expire after 30 or 60 days (can't remember for sure) but it will expire and you will periodically see popup reminders notifying you that you need to complete the SBS install. You would need to load Windows STD or something else with a license on the server.
Hidden advantages of using the same IT vendor for years
Posted by Peter Heinicke on 11/30/11 9:21 PM
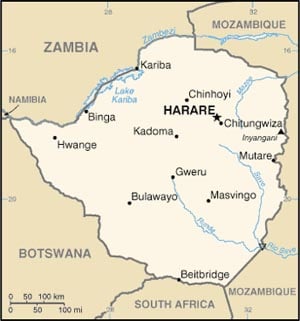
In 1990 and 1991, PC Methods was instrumental in providing a complete workstation and power conditioning system to Living Bible Translators in Harare, Zimbabwe. We learned about six lessons that will still apply to setting up systems in other countries.
Tags: IT services, Backup, St. Charles PC Repair, Fox Valley PC Support
Desktop or Tablet PC, Which one is best for St. Charles?
Posted by Peter Heinicke on 7/31/11 7:57 PM
Unless you've been living under a rock for the past year or so, you're well aware of the tablet computer phenomenon, mainly as evidenced by the meteoric rise of the Apple iPad. In its last financial report, Apple stated that it had sold 9.25 million of the hand-held devices in the quarter ended June 25, 2011, which makes the iPad a bigger seller than PCs sold by leading companies like Dell and HP. Meanwhile, another wave of tablet computers, all based on the Android operating system, is hitting the market from HP, Acer, Archos, and Samsung. Is the tablet computer essentially replacing the PC? Or does the PC - and we'll include traditional laptops in this category - still have a role to play in business and in the home?