Automated tools like anti-virus software, firewalls, and other computerized security technology can only go so far to eliminate the threat posed by a small army of professional hackers. Like most crimes, the human element is critical for the cyber crime to be successful. To combat this, I sorted out 7 urgent reasons why you need to create your "human firewall" as soon as you possibly can. Employees are your last line of defense and need to become an additional security layer when attacks make it through all your technical filters.
Your users need to be trained to become a human firewall against cyber attack
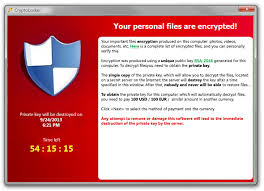
- Phishing leads the IRS dirty dozen of scams
- Phishing is the use of phony email to obtain information or compromise systems. The Internal Revenue Service rounded up some of the usual suspects in its annual look at the Dirty Dozen scams you need to watch out for this year. It should come as no surprise that the IRS saw a big spike in phishing and malware incidents during the 2016 tax season because the agency has been very public about its battle with this scourge.
Read More
Tags:
Anti Virus,
ransomware,
phishing,
vishing,
spam
On Saturday, April 26, 2014, Microsoft Corp. reported to the United States Computer Emergency Readiness Team (a division of the Department of Homeland Security) that Microsoft Internet Explorer versions 6-11 had come under attack! Malicious hackers were exploiting a use-after-free vulnerability that could allow unauthorized remote code execution. This could lead to the complete compromise of an affected computer system.
Read More
Tags:
Blogging,
Blog,
IT Support,
Anti Virus,
Microsoft,
Internet Explorer
PC Methods offers a five block support offering for our IT clients. Not all clients choose to take advantage of all five blocks, but they are there if you want the best possible combination of value and service. The blocks are: Project Work, Centralized Services, Network Administration, Virtual CIO, and Support. These are the product offerings that clients should look for when selecting the best possible IT business partner.
Read More
Tags:
IT services,
Disaster Recovery,
Backup,
Backup to the cloud,
Cloud Computing,
Blogging,
Blog,
Anti Virus,
Virus Removal,
computer repair,
Symantec,
Malware,
Security Software,
Small Business,
Sage 300 ERP
“The universe is so very complicated," said Dr Dimble.
Read More
Tags:
Anti Virus,
Virus Removal,
Symantec,
Malware,
Security Software